Cybersecurity and information technology are two different things but they are used interchangeably most of the times.how do they differ?
As we have already discussed in the previous article that how Python language is becoming popular among Computer programmers and technocrates. Now we will discuss the future scope of Python language and it’s industry requirements. Future Technologies are Putting Trust …
Python is one of the fastest growing languages and has successfully completed the span of more than 25 years if you talk about its adaptation. This reveals a promising future scope of python programming language. It has been continuously serving …
Digital marketing helps you reach a large number of audience than you could reach through the traditional methods of marketing, and target the prospects who are most interested in buying your product or service. In fact, it’s often more cost-effective …
Information Technology offer countless benefits for education industry. If implemented correctly it enhances the learning experience of students, improve communication among teacher, students & parents as well as improve the productivity of admin and other staff members. Information technology fosters …
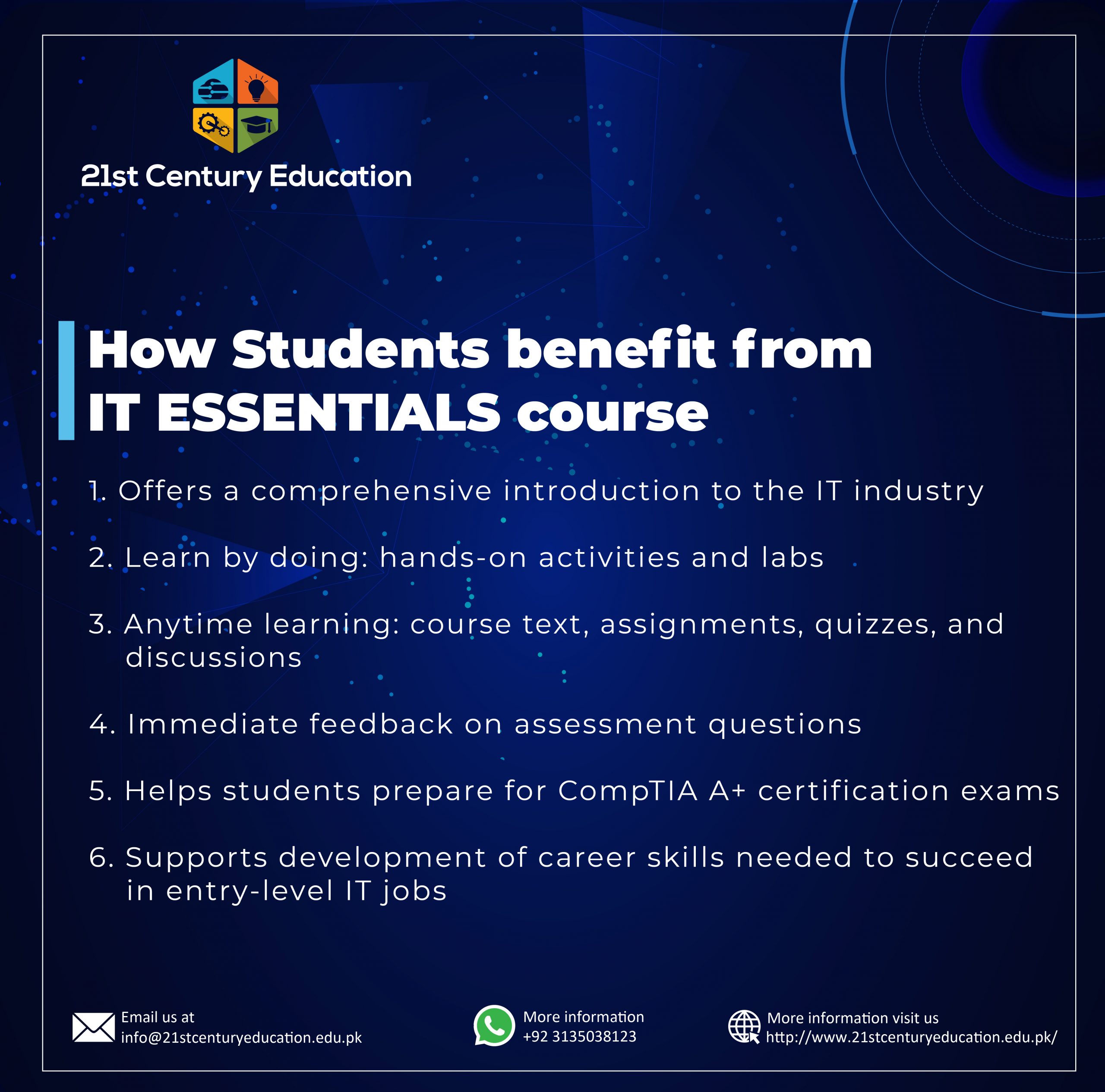
21st Century Education is offering CISCO IT Essential Course ONLINE under the supervision of highly qualified trainers. You cm check the course details HERE.
Information technology and business are becoming inextricably interwoven. I don’t think anybody can talk meaningfully about one without talking about the other (Bill Gates) So, if you are planning to be Entrepreneur or networking or cybersecurity, you should get your …
Communication is a vital leadership skill, and the Digital Age has changed the way people communicate. While technology contributes to the noise that often distracts or interrupts people from sending or receiving messages effectively, it can be a great asset …
Do you know how to counter these security attacks? Here are some common cyber security attacks Malware. Malware is a term used to describe malicious software, including spyware, ransomware, viruses, and worms. Man-in-man middle attack Phishing DoS attack Zero-day exploit …